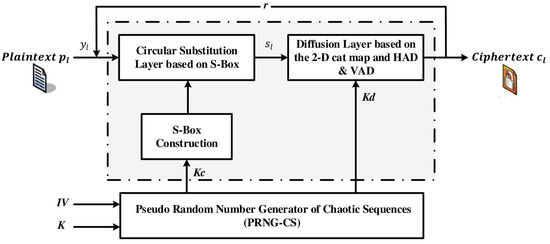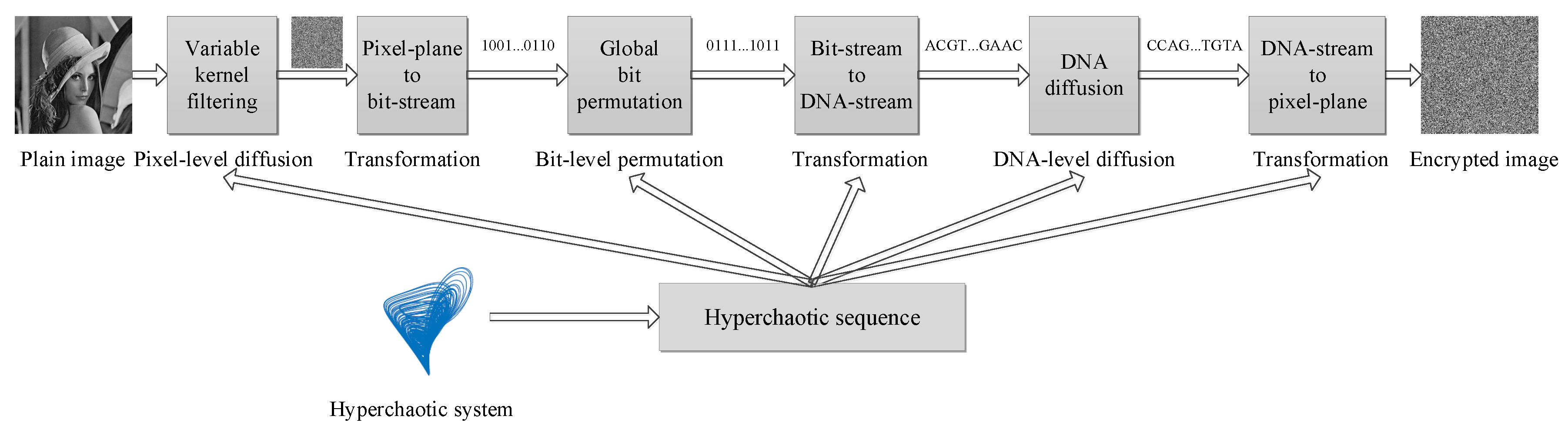
Entropy | Free Full-Text | A Novel Image Encryption Approach Based on a Hyperchaotic System, Pixel-Level Filtering with Variable Kernels, and DNA-Level Diffusion
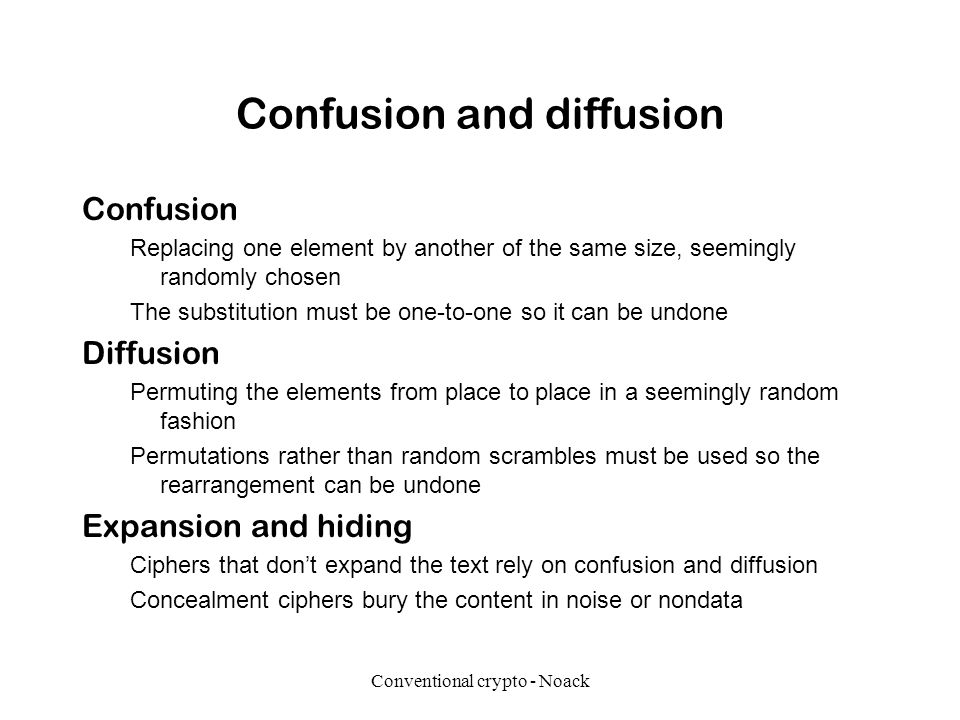
Conventional crypto - Noack Conventional crypto Diffusion and confusion How Mary Queen of Scots lost her head Various hand operable ciphers Various Enigmas. - ppt download

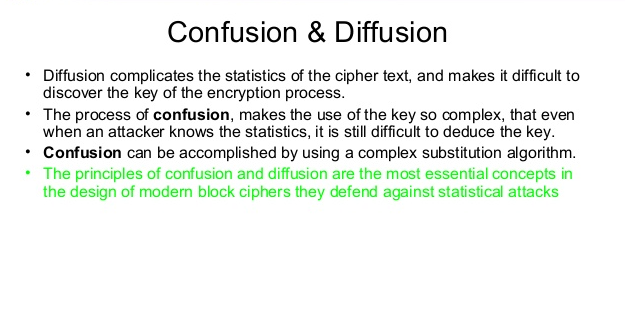
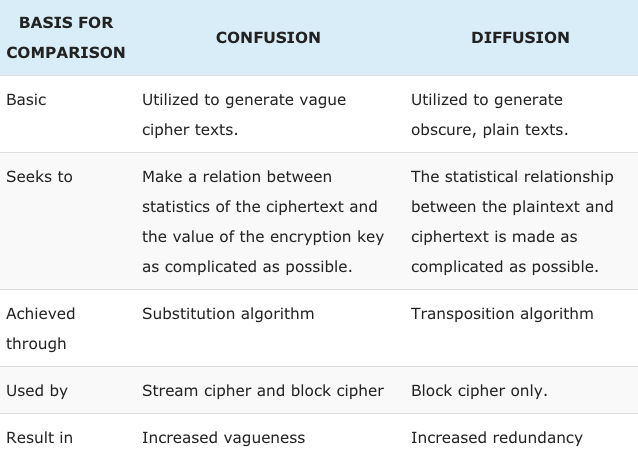
Confusion and Diffusion1 Ref: William Stallings, Cryptography and Network Security, 3rd Edition, Prentice Hall, ppt download

Filters In Halftone Visual Cryptography Via Error Diffusion: Analysis and Enhancement: Sharma, Anshul, Agrawal, Sunil: 9783659250439: Amazon.com: Books

CISSP PRACTICE QUESTIONS – 20200308 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Confusion | Diffusion | Confusion Vs Diffusion | Frustate statistical Cryptanalysis | Shannon Method - YouTube