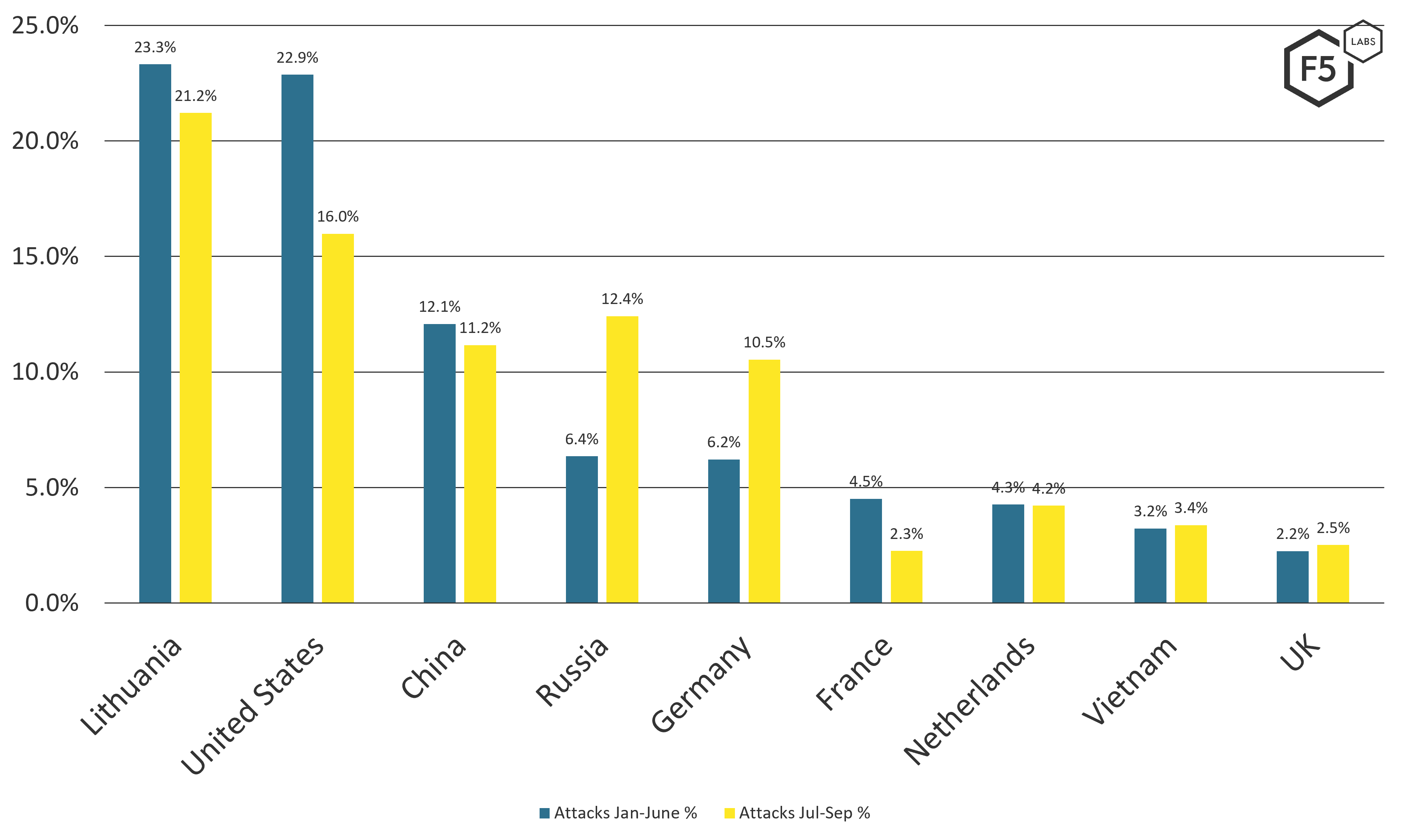
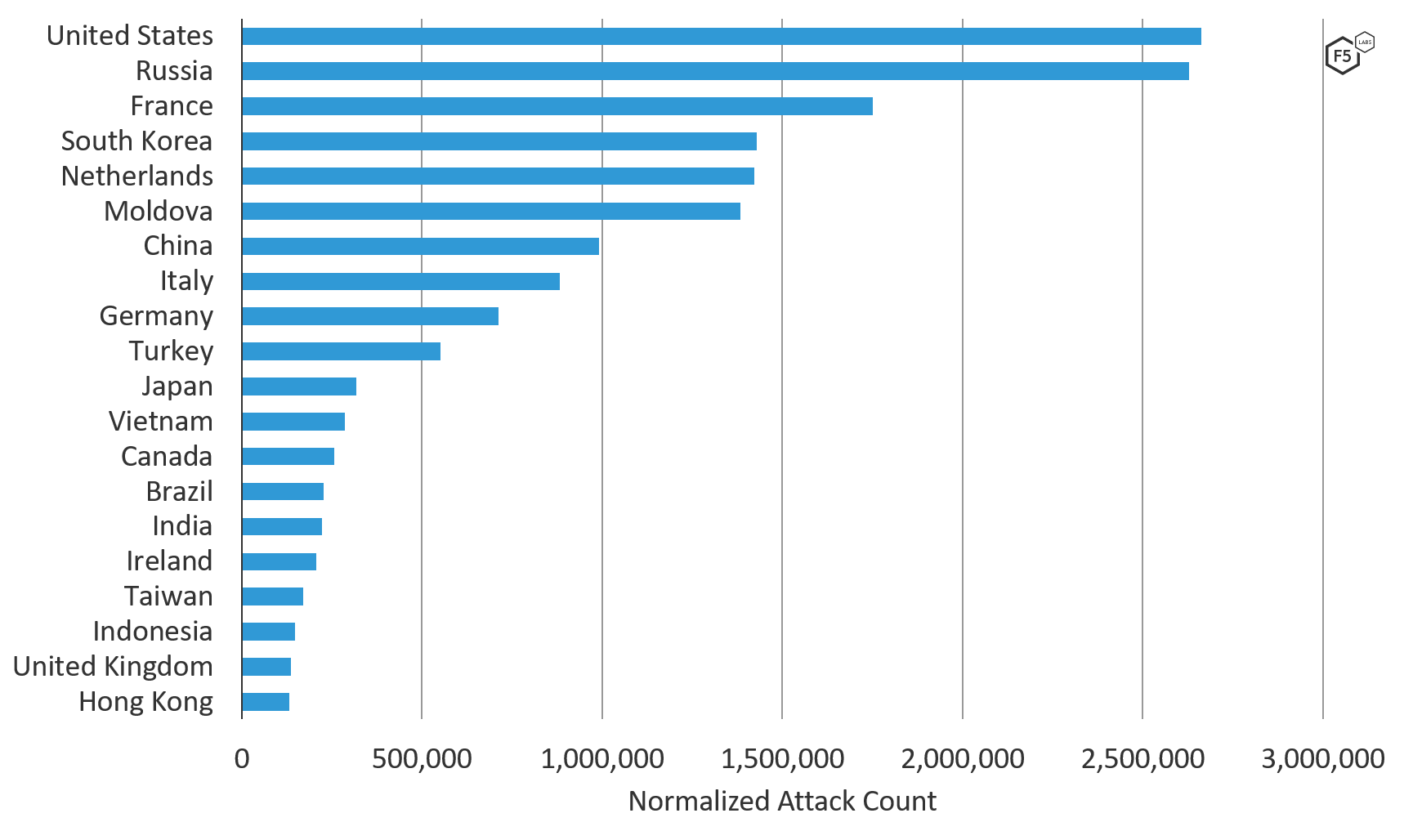
Top attacking countries Some of these attack sources can be innocent... | Download Scientific Diagram

KPMG on Twitter: "Top 10 sources and targets of #cyber attacks by volume via @NorseCorp https://t.co/2FMbpo2nHU #CEOoutlook https://t.co/NoUBB39JXT" / Twitter

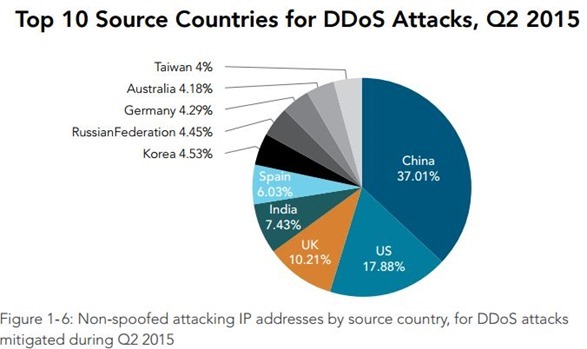
a Top Network attacks in 2015: (Source McAfee Labs 2015). b Top Network... | Download Scientific Diagram


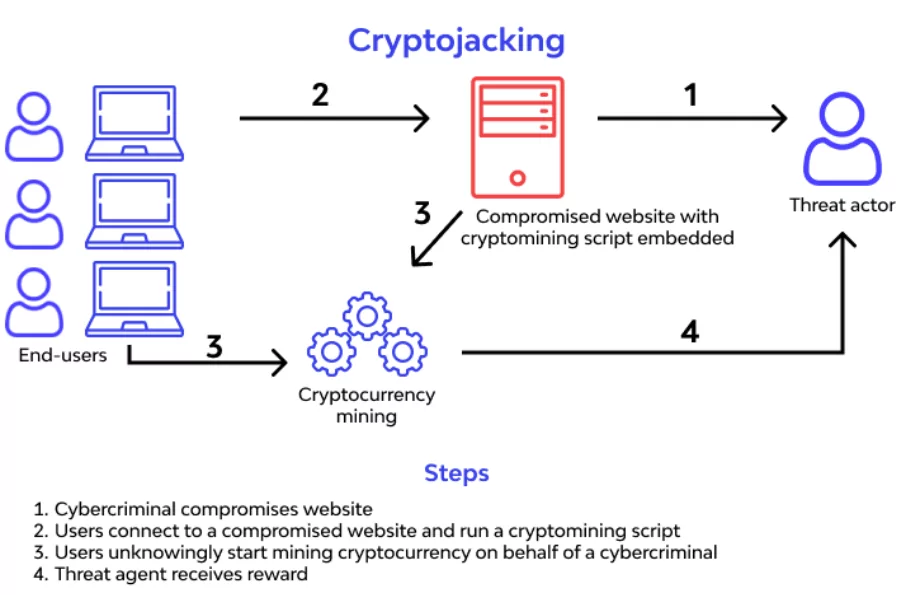







.png)